In our previous article we highlighted how the modern world has placed Healthcare firmly in the crosshairs of cyber criminals, and we briefly explored some of the methods cyber criminals use to attack your systems – in the process stealing patient data and causing disruptions to service. We will now look at two of the cyber threats we looked at in the previous article, Phishing and Ransomware, and explain how to reduce the risk of an attack being successful.
Phishing scams and Ransomware attacks have become two of the most popular forms of attack for cyber criminals all over the globe. This is due to the ease of which an attack can be completed successfully.
There are ways to combat them though, and these methods may not be what you expected.
Combat Phishing and Ransomware Attacks
No, we aren’t going to recommend an expensive tool that you will have to implement around the entire practice, but instead we would simply recommend educating your team on what a Phishing Email looks like, and what the red flags are to look out for. Let’s look at an example of one now.
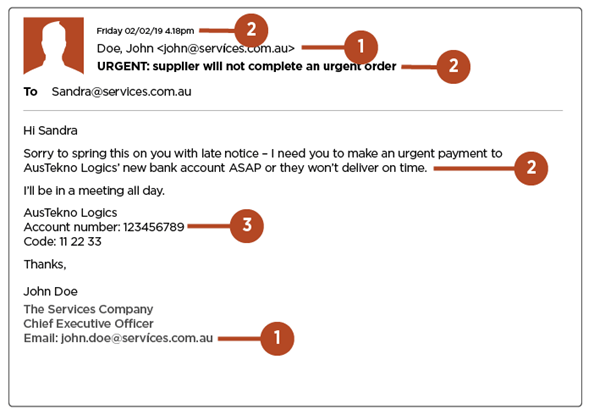
We will now explore the elements of this email that may cause you to not trust the recipient, in turn meaning it could be a Phishing Email and potentially contain a link to authorize a Ransomware attack.
- It is impossible to know who the Email is from; business and professional emails shouldn’t look like ‘normal’ email addresses. If you cannot be certain of the validity of an email address, check it. We all glance over email addresses to check them, but look closer – the “i” in “services” is, in fact, a different character. These differences are very hard to spot, but it is worth taking the time. If the recipient claims to be someone you have communicated with before then simply create a new email and message them with the trusted email you already know – if they confirm it then great, and if they don’t then you know the original was a scam.
- Most professional Emails won’t put you on the spot like this; there is too much urgency in the message. As we covered in the previous article, scammers create a sense of urgency to encourage you to behave in a certain way without any forethought. DON’T RUSH but take your time. It is integral before moving on that you find out if the email is genuine or not.
- Always verify changes to payment details directly – NEVER deviate from company procedure regarding payment. It may be quicker to do it yourself this way, but if company procedure takes you through the accounting team, then back to finance, on a long laborious journey, then so be it – you would rather that then it be you that hands over money to a cyber criminal.
The only difference between a Phishing Scam and Ransomware scam is that this Email doesn’t have a link embedded, so follow the same procedure of vigilance when links are present too. You must always proceed with care, examine links closely and if you are in any doubt walk away or get advice from a superior member of staff.
These are just some of the ways to combat Phishing and Ransomware attacks. Take your time and be certain before you act – and instruct your team to do the same.
Your Business – Prepared and Secure
At Grapevine, our team of dedicated engineers can meet any technical challenges you may come across. We take our time in getting to know you, your business, your employees, and your goals for the future so we can then find the best technological solution for you to guarantee constant security and progression. Our years of experience leave us primed and ready with all the tools needed to ensure a top-quality service, now and into the future. Contact our team and let us start our journey together today.


