
Phishing is a type of social engineering attack where the attacker sends a fraudulent message designed to steal user data or deploy malicious software like ransomware. The attacker masquerades as a trusted business entity to dupe you into opening an email or text message in an effort to access critical information.
What is phishing and why is it so common?
Phishing is a huge threat and growing more prevalent each year. In 2021, phishing attacks were responsible for more than 80% of reported security incidents and as much as 90% of data breaches.
Cybercriminals, posing as legitimate businesses, use phishing as an attempt to obtain sensitive information from individuals, usually via email. Analogous to fishing, attackers generally “fish” for your private information like usernames, passwords, and credit card numbers.
An analysis of over 55 million emails revealed that one in 99 emails is a scam. This shouldn’t be a huge surprise given that phishing, compared to other forms of cyberattacks, is relatively simple. Phishers don’t need to infiltrate a system or your infrastructure to be successful, they simply need to get one person to click on an email or link. Most phishing emails have a few common features, such as a sense of urgency, attachment or link, and an unusual sender.
Examples of phishing attacks
While scammers are getting increasingly more sophisticated, there are some general clues you can look for to help avoid a phishing attack. Grammatical errors, low-resolution logos, or a strange URL are all indications of an illegitimate email. Before clicking on an embedded link, hover over it and see if it matches that of the company sending the email.
We know that phishing occurs when a victim replies to a fraudulent email demanding some kind of urgent action but that can take on various forms. Some examples of requested actions in a phishing email include:
- Clicking an attachment
- Enabling macros in Word document
- Updating a password
- Responding to a social media connection request
- Using a new Wi-Fi hot spot
One common thread that runs through all types of phishing emails, including the examples below, is the use of social engineering tactics. Like most phishing attacks, social engineering preys on the natural human tendency to trust people and companies.
This leads to many users failing to carefully review phishing email details and automatically trusting the sender’s request. Email phishing victims believe they’re helping their organizations by transferring funds, updating login details, or providing access to proprietary data.
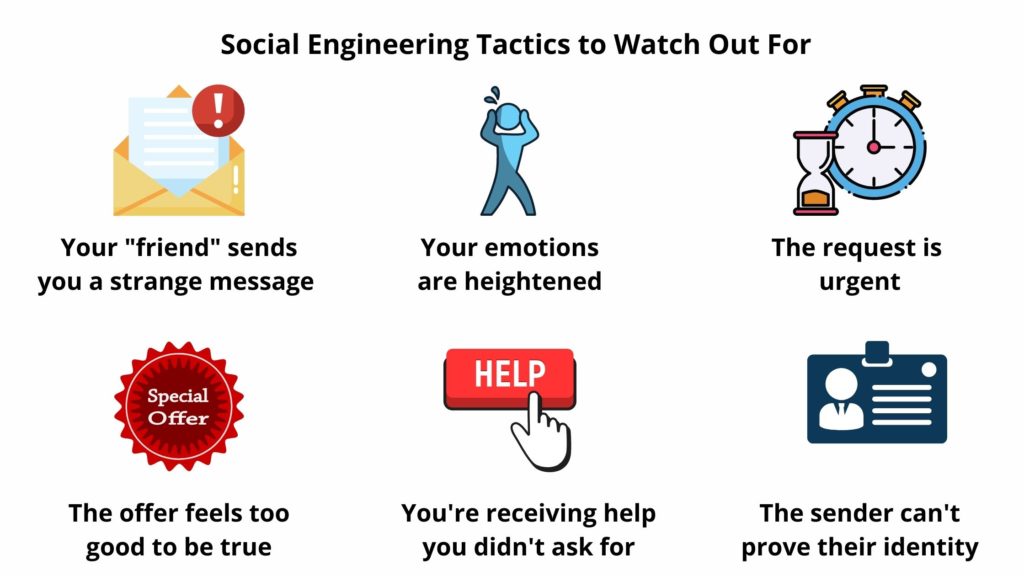
Cybercriminals are always evolving and it’s impossible to maintain a comprehensive list of all types of attacks but you can familiarize yourself with the most common forms of phishing to help protect yourself and your business.
Below are three examples of common Phishing emails:
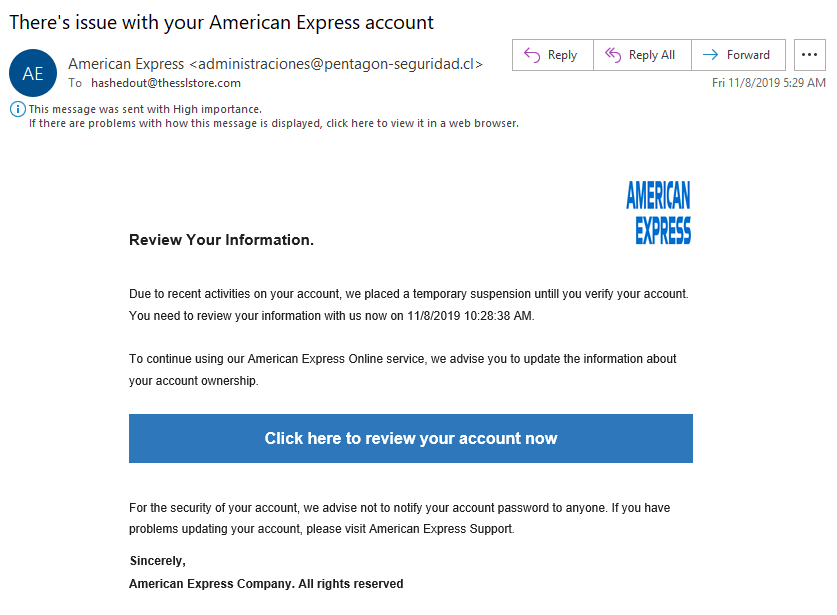
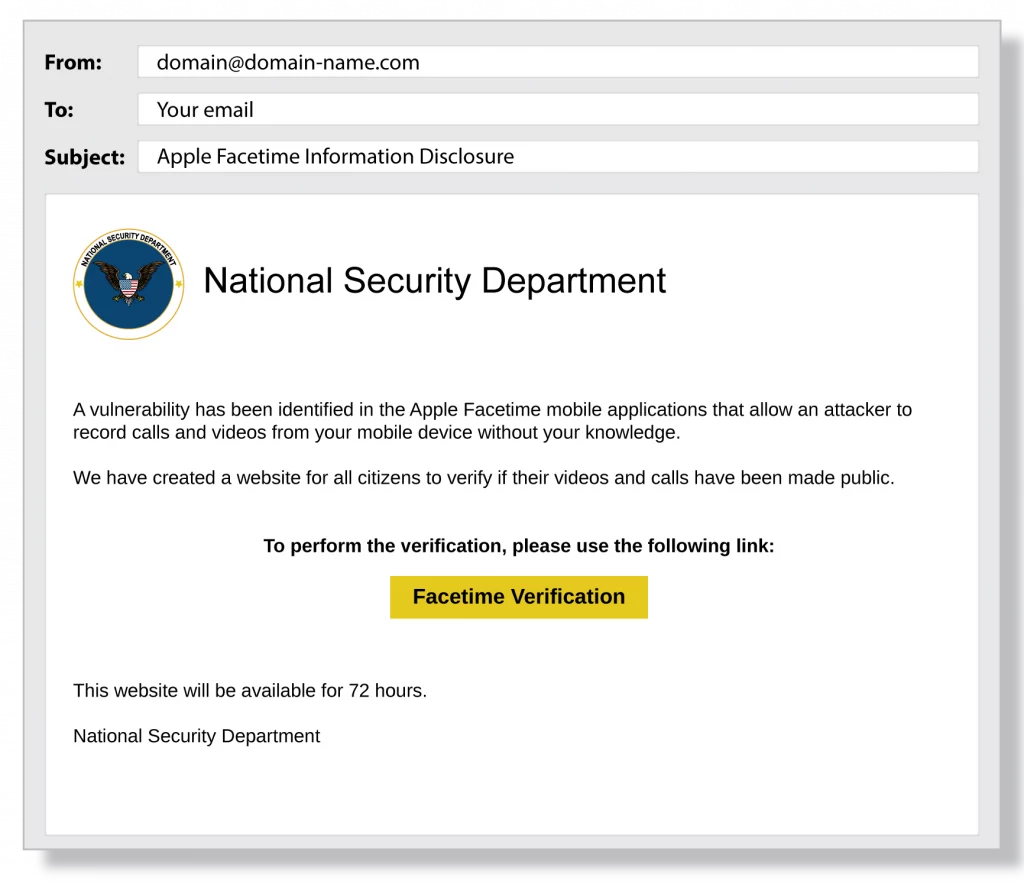
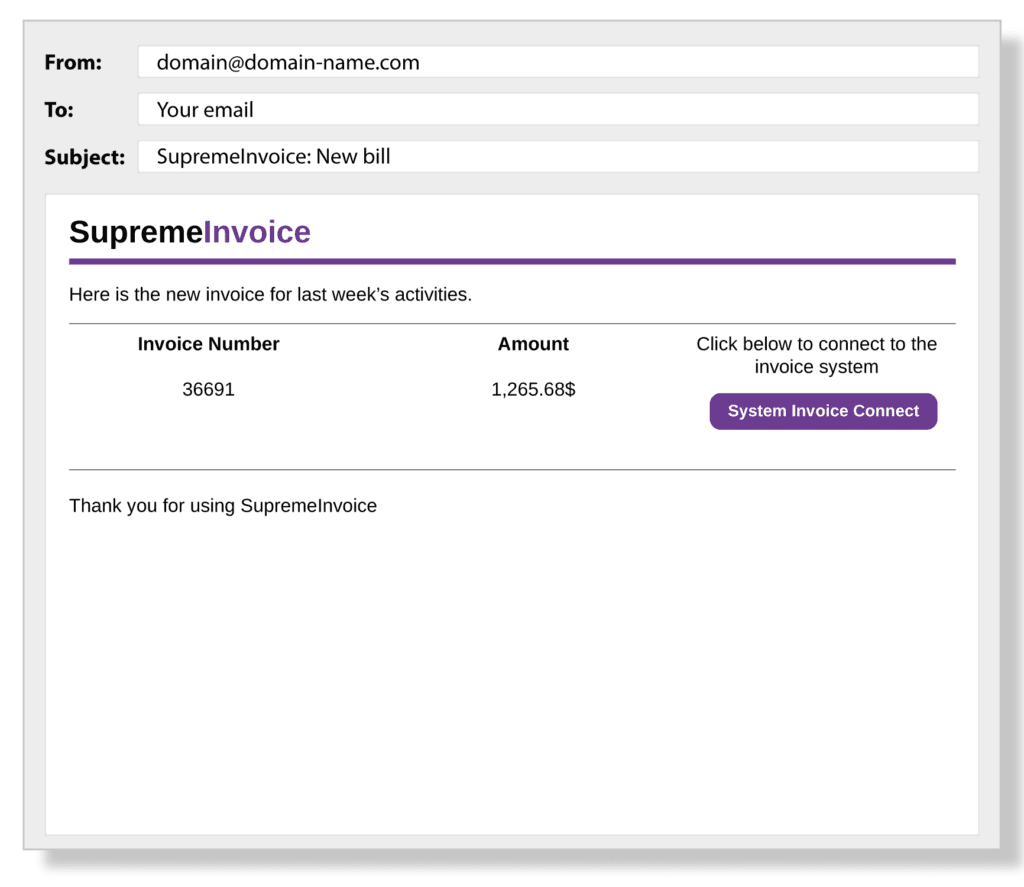
How To Protect Against Phishing Emails
To protect against phishing emails, you need to raise awareness of how phishing happens. When people experience first-hand how easy it is to be tricked by what looks like a valid email, they are more likely to carefully review email details before automatically clicking Reply, an embedded link, or downloading an attachment.
To protect against phishing emails, remember these five keys to building a cyber secure aware culture:
- Educate: use security awareness training and phishing examples to educate, train, and change behavior.
- Monitor: use phishing simulation tools to monitor employee knowledge and identify who is at risk for a cyber attack.
- Communicate: provide ongoing communications and campaigns about phishing emails, social engineering, and cyber security.
- Incorporate: make cyber security awareness campaigns, training, support, education, and project management part of your corporate culture.
You want to be protected from phishing email attacks. The same sentiment extends to your colleagues, organization, friends, and family members. Everyone must be able to keep their information safe
The best way to do this is to create optimal levels of cyber security awareness. The first step is finding out who is at risk for a phishing attack.
Now more than ever, it’s critical to partner with a leader in cyber security to protect yourself and your business assets from phishing and other cyber breaches. Grapevine MSP can help secure your business from online threats like phishing, ransomware, malware, and more. Contact us today to get started.

