No company wants to experience a data breach. Yet sadly, it’s difficult to totally escape them in the atmosphere of today. At 83% of the firms, there have been several data breaches.
Several ways exist for these breaches to harm enterprises. The immediate cost of fixing the breach comes first. The expenses of missed productivity are another factor. To that, you can also add missed sales and eroded customer confidence. A breach may also result in high legal fees for the company.
The cost of a data breach, according to a report by IBM Security, increased once more in 2022. One breach currently costs $4.35 million globally, an increase of 2.6% from the previous year. If your company is located in the US, the price jumps to $9.44 million. Companies in Canada incur an average loss of $5.64 million due to data breaches.
Smaller businesses typically have slightly cheaper costs. But SMBs are frequently more severely hurt by breaches. They lack the resources larger businesses have to cover all those expenses.
According to estimates, 60% of small businesses fail within six months of a cybersecurity incident.
Businesses don’t have to accept the certain fate of a data leak. They can reduce the prices by utilising some tried-and-true strategies. These cybersecurity procedures can reduce a cyberattack’s potential harm.
These conclusions are all drawn from the IBM Security report. They contain specific data on the advantages of enhancing your cybersecurity strategy.
Cybersecurity Tactics to Reduce the Impact of a Breach
Use a Hybrid Cloud Approach
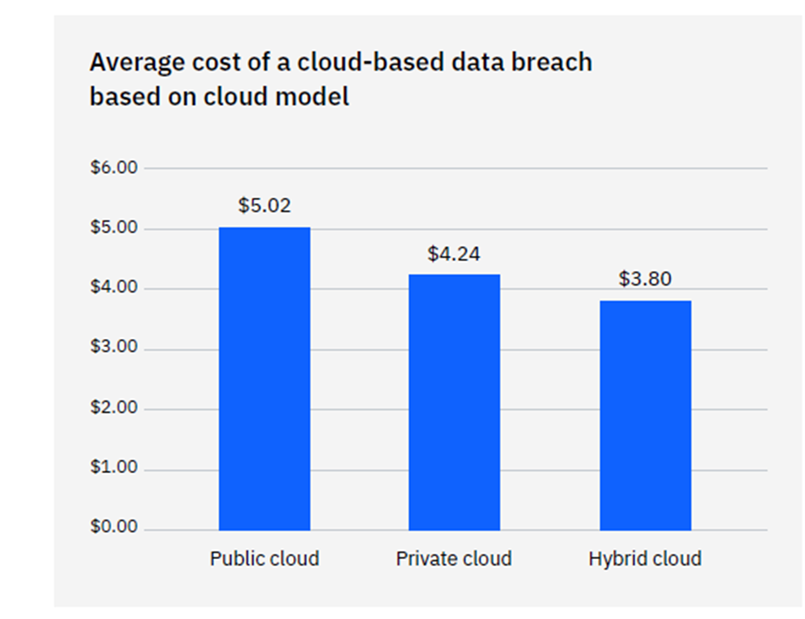
For data storage and business operations, the majority of enterprises use the cloud. According to research, the cloud is the location of 45% of all data breaches. Yet not all cloud computing techniques are made equal.
Breach costs in a hybrid cloud are far lower than those in a public cloud. A hybrid cloud is what? It denotes that some processes and data are stored in a private cloud environment and others are in a public cloud.
Some people might be surprised to learn that employing a hybrid cloud strategy was superior to a private cloud.
Put in Place an Incident Response Plan & Practice It
An incident response (IR) plan can be written by a small business as well as a huge corporation. The IR plan is nothing more than a collection of guidelines. Employees must abide by it in the event that any number of cybersecurity issues take place.
Here’s an illustration. Disconnecting the infected device should be the initial action in ransomware cases. The effectiveness and quickness of a reaction to a security crisis are improved by IR planning.
An incident response strategy that has been tested lowers the cost of a data breach. It reduces it by $2.66 million on average each event.
Adopt a Zero Trust Security Approach
A group of security mechanisms known as zero trust combine to strengthen a network. A handful of these are, for instance:
- Multi-factor authentication
- Application safelisting
- Contextual user authentication
The adoption of zero trust is still lacking in 79% of critical infrastructure enterprises. Costs related to data breaches can be greatly decreased by doing this. Companies who don’t use zero trust strategies pay an extra $1 million for each data breach.
Use Tools with Security AI & Automation
Using the appropriate security measures can significantly reduce the expense associated with a data breach. The biggest expense savings came from using security AI and automation tools.
The cost of a data breach was reduced by 65.2% as a result of automation and AI security solutions. Advanced threat protection is one of these types of solutions (ATP). Applications that look for dangers and automate the reaction may also be included.
How to Get Started Improving Your Cyber Resilience
Several of these techniques for reducing the cost of data breaches are just standard practises. Starting now, you can implement updates to your cybersecurity strategy one at a time.
Create a roadmap with the assistance of a reliable IT service company. The “low-hanging fruit” should be addressed first. Continue with longer-term endeavours after that.
Multi-factor authentication would be an illustration of “low-hanging fruit”. It is inexpensive and simple to implement. Also, it greatly lowers the chance of a cloud breach.
Developing an incident response strategy could be a longer-term task. After that, you would create a schedule for your team to practise the plan on a regular basis. You could work out any kinks in those drills.
Need Help Improving Your Security & Reducing Risk?
Partnering with a reliable IT partner relieves you of a lot of the security-related stress. Call us right away to arrange a discussion about a cybersecurity plan.


